Broadband Corp., a Hutchinson, MN-based company supporting the area’s commercial and residential needs for high-speed internet, is excited to announce that its website is live! Besides having a fresh new look and feel, the website also reflects the latest information on Broadband Corp's products and services, coverage area, and …
Main Content
High-Speed Internet for Rural Communities in Central Minnesota
Whether you are on the farm or in town, we can keep your home or business connected with reliable and affordable internet.
Enjoy the Speed & Simplicity of Internet in Rural MN
Get our fiber fed network for fast internet no matter where you are. No phone line or satellite dish required.
- Blazing fast internet for life’s demands
- Plans starting at just $49.99 a month
- Unlimited usage
- Local Service from a hometown company since 2004
EXPANDING SERVICE TO YOUR AREA
![]()
Online Support
We are here to help! With our Ultimate Support service every digital device in your home can be supported by our helpful staff.
![]()
Services
Our high-speed internet has plans starting at just $49.99 a month!
![]()
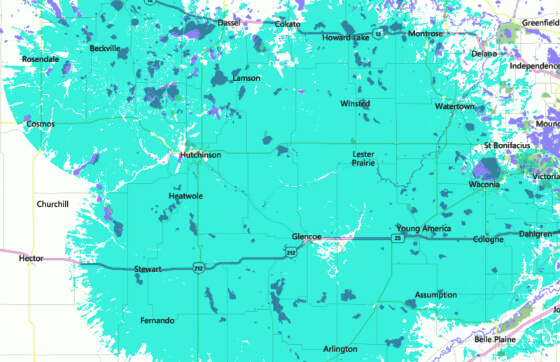
Coverage Area
Our service area includes farms and cities in Meeker, McLeod, Carver, Wright, & Sibley counties.
Footer
Contact Us
Broadband Corp.
Broadband Corp. is a Hutchinson, MN based company supporting commercial and residential communication needs, bringing internet services to rural area residence and business using state of the art technology.